A deadly botnet may lurk in your old router and any IoT (Urgent Consumer Advice)

A deadly botnet has been lurking in internet-connected older routers, web/IP/security cameras, DVRs, and many IoT devices. With the flick of a virtual switch, an enemy state could disable the Internet. Hello, cyber warfare.
The Federal Bureau of Investigation (FBI), Cyber National Mission Force (CNMF), and National Security Agency (NSA), supported by the Australian Signals Directorate and other world security agencies, have just released a chilling report that unambiguously states that the People’s Republic of China (PRC)-linked cyber actors have compromised hundreds of thousands, if not many millions, of Internet-connected devices, including routers, firewalls, network-attached storage (NAS) and Internet of Things (IoT) devices to create a deadly botnet – a network of compromised nodes poised to inflict massive damage.
The report states that exposed device manufacturers and owners must update and secure these devices to prevent them from being compromised and joining the botnet.
What is a deadly botnet?
A botnet gets commands from an internet Command and Control server to do something. It might be part of a DDoS (Denial of Service attack), stealing keystrokes and data, controling devices, sending fake emails, or infecting more IoT devices.
A botnet may be sitting idle on your device. You would only suspect something wrong if you had an internet traffic sniffer that helps identify what your router or IoT device sends to the internet.
Since 2016, Chinese state cyber actors have been developing and refining the Mirai malware family. This self-replicating, mutating system roams the internet, infecting exposed devices in North America, South America, Europe, Africa, Southeast Asia and Australia.
Older Wi-Fi 5 N or earlier routers are the most at risk
You probably would never know, but your old router could be silently infected and part of a global botnet, especially if it is a W-Fi 5 AC or earlier model.
It does not affect every old router or brand—just those running a Linux operating system that has never been patched. The following are known examples.
Routers sold in Australia include:
- Arris
- ASUS
- Zyxel
- DrayTekVigor 2960/3900/300B,
- Cisco (RV340/345)
- Netgear (many pre-08/21)
- D-Link (DIR-818/822/895/868/869/880/890, DWL-2600AP)
- TP-Link (AX1800/3000/5400 and Deco X50 and XE200) – all have patches
- Telstra’s White Smart Modem Gen 2 (firmware before 0.18.15r)
- Any generic Chinese device
The list is not exhaustive; it is at risk if your router has not received a firmware patch in the last year or so.
It also affects
- Network-attached storage from QNAP and many more devices.
- Unpatched Windows 10 Server 2016,
- WordPress and PHP (8.1 using Apache on Windows)
- Hikvision, Duha, Panasonic (and consumer white-labelled) IP cameras using Linux. See UK joins others in banning Chinese-made security cameras
- DVRs
- Almost any ‘generic’ device with an ARM processor that connects to the internet, like smart speakers, light controllers, thermostats, cameras, doorbells, etc.
The deadly botnet danger
What if millions of devices started a DDoS (flooding the internet with traffic)? It happens regularly and is like a massive swarm of mosquitoes attacking you.
In October 2023, a DDoS attack using Mirai-infected devices peaked at 398 million requests per second. Security reasons prevent details, but the attacks were on cloud storage (AWS, Azure, Google, etc.).
In June 2020, a four-day attack on web page hosting sites aimed at 316,000 web pages peaked at 754 million requests per second.
There are millions of DDoS attacks every day.
How to check if a deadly botnet lurks within
It is hard—no consumer app can detects IoT devices infection. An online Port Forwarding Tester can manually test for ‘Scan all common ports’ that may help you identify if your router is vulnerable. The result should be that all ports are ‘closed’ and if any are open, you are likely infected. The easiest cure is to buy a new modem/router/mesh system from D-Link, Netgear, ASUS, or TP-Link (all their Wi-Fi 6, 6E and 7 products are secure).
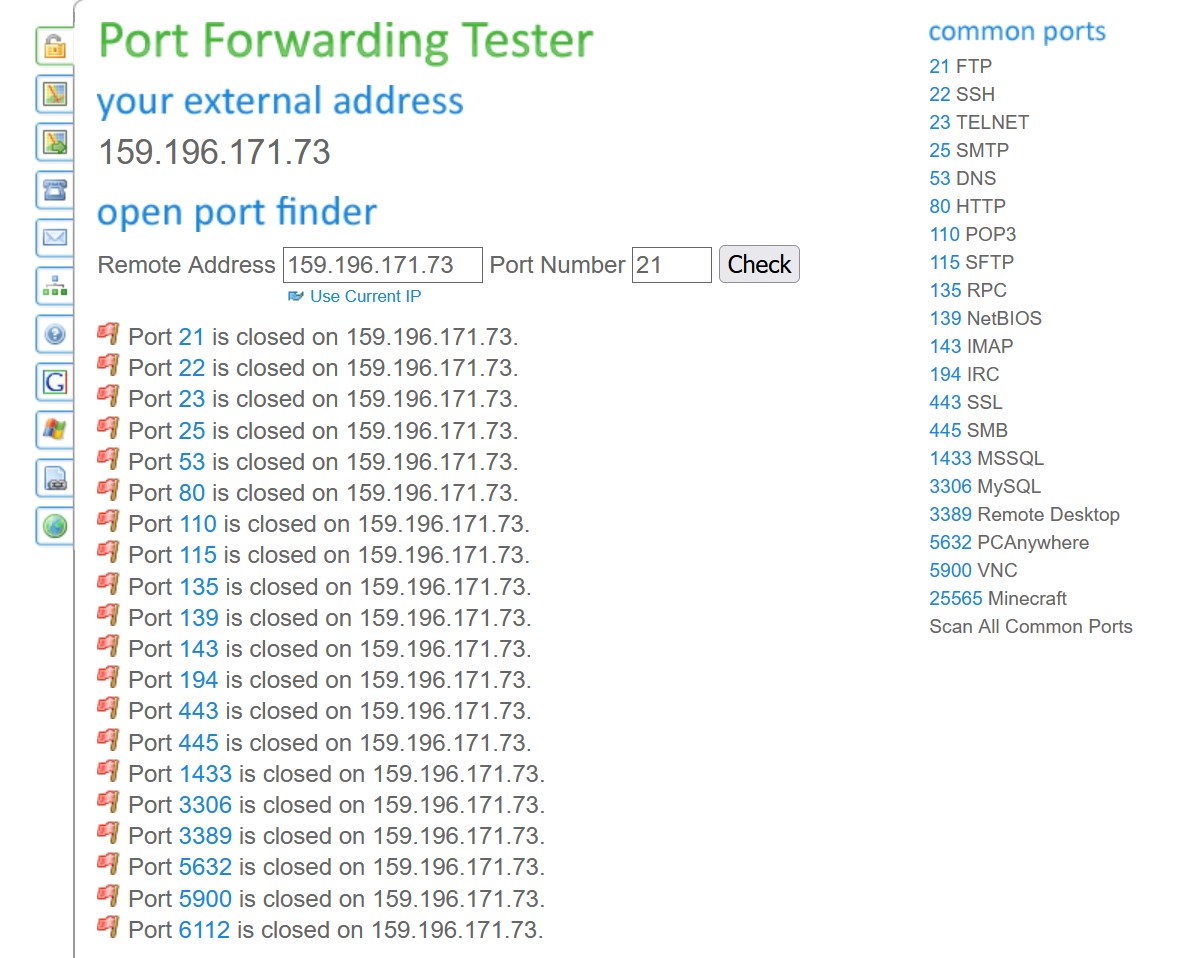
More sophisticated internet packet/traffic sniffers, really the province of network experts, can identify if your network is uploading more than it should. Still, you must manually identify each device by taking each offline until the practice stops. It cannot determine if the device is dormant, waiting for command and control instructions.
An older router is the most likely suspect. The easiest way to access it is via the manufacturer’s app or inbuilt web server admin page. You need to know your administration login and password to get in. Change the admin password to a hard-to-break one (at least 16 alphanumeric and symbols). Mirai got in because so many routers had admin/admin!
Look for firmware updates and install them. If the current firmware is 2022 or earlier, your router may be a Mirai target. The best advice is to buy a new Wi-Fi 6, 6E or 7 router or mesh system.
You can then protect all your home networks using Trend Micro Home Network Security, which has a ‘black box’ to filter internet traffic and prevent attacks. I would not dream of surfing the net without this protection.
CyberShack’s view – Can the internet be shut down? You bet
The FBI states that deadly botnets could shut down essential services and the internet itself. However, as China’s internet sits behind the “Great Firewall of China,” it is safe from attack.
It could also attack IoT infrastructure, such as solar batteries, smart meters, security cameras that use the web for cloud storage and, more recently, AI-based control and identification.
There is also the possibility that all cloud-connected devices, such as electric vehicles, could be shut down. Read Weaponised Tesla Cybertruck remotely disabled in battlefield.
This could potentially be used to disrupt the internet globally, a scenario that could start a real cyber war.
Think we are kidding, overeating, and the sky is falling? Sorry no.